When processing and exchanging sensitive data, special attention should be paid to secure encryption. It is essential for protecting the contained information from unauthorized access.
The various encryption technologies used nowadays are no longer considered a niche topic in the tech industry, but have rather become a topic the mainstream society is aware of. Even the German government now calls for a "right to encryption", which is intended to increase the general acceptance in society and to protect fundamental rights, such as privacy and the confidentiality of communication.
We will therefore take a closer look at the various encryption methods, explain why SSL encryption alone is not enough, and how sensitive data can actually be protected in the best possible way.
What is meant by HTTPS and SSL/TLS?
Today, TLS (Transport Layer Security) and SSL (Secure Sockets Layer) basically describe the same form of data transmission, whereas SSL is the predecessor version of TLS. Yet, the term SSL is usually used.
SSL/TLS
SSL is the common name for an encryption protocol for secure data transmission. When information is transmitted from one system to another, SSL encryption prevents the information from being read by third parties. This is done by using algorithms that encrypt the data during transmission. Data that must not fall into the hands of third parties or even criminals, such as bank data, is thus protected from unauthorized access during transmission.
HTTPS
Everyone knows the abbreviations http:// and https:// from the URL bar of their browser. From a technical point of view, there is no difference between HTTP (Hypertext Transfer Protocol) and HTTPS (Hypertext Transfer Protocol Secure) since the protocol is identical for both variants. The crucial difference is that HTTPS, unlike HTTP, uses an SSL certificate and thus encrypted transmission. Additionally, a small padlock in your browser symbolizes this secure connection.
But why is SSL encryption alone not enough?
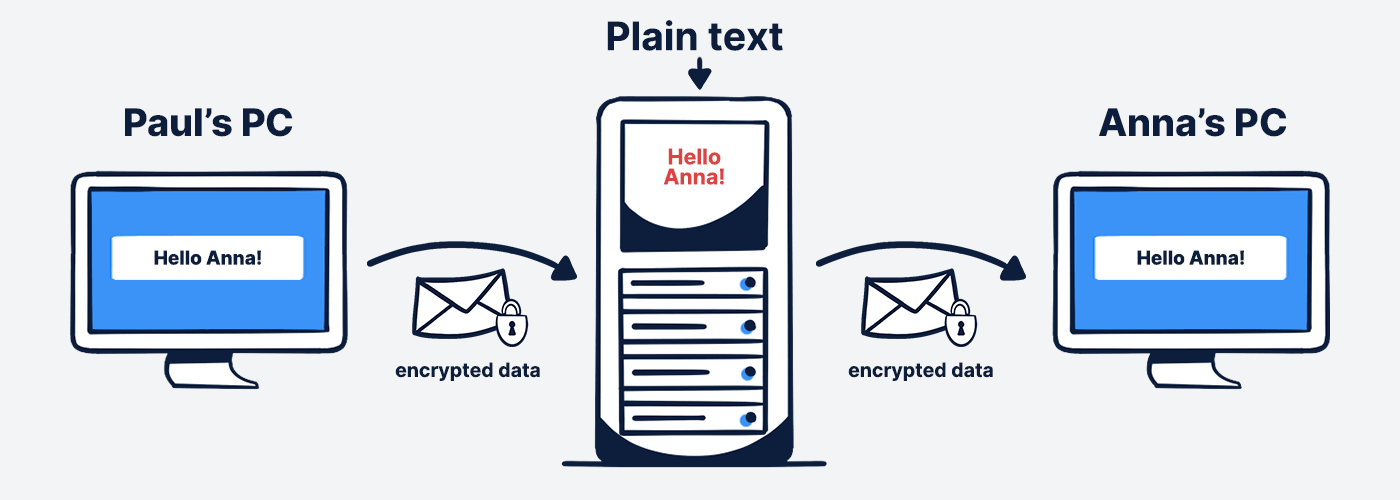
SSL/TLS thus encrypts data in transmission between the client server and the web server (e.g., when your information is transmitted to the servers of a cloud provider).
But what happens once the data reaches the server?
If the provider does not take any additional measures, the data is decrypted again after secure transmission and is stored in plain text on the servers. Then no one can access them while they are being transmitted, but on the servers, they can theoretically be viewed by the provider without encryption.
Client-side end-to-end encryption
If you want to protect your data in the best possible way and also eliminate the security gap of SSL encryption, you should work with client-side encryption (end-to-end).
The following images illustrate the difference between client-side end-to-end encryption and the aforementioned server-side SSL encryption:
Server-side SSL encryption:
Client-side end-to-end encryption:
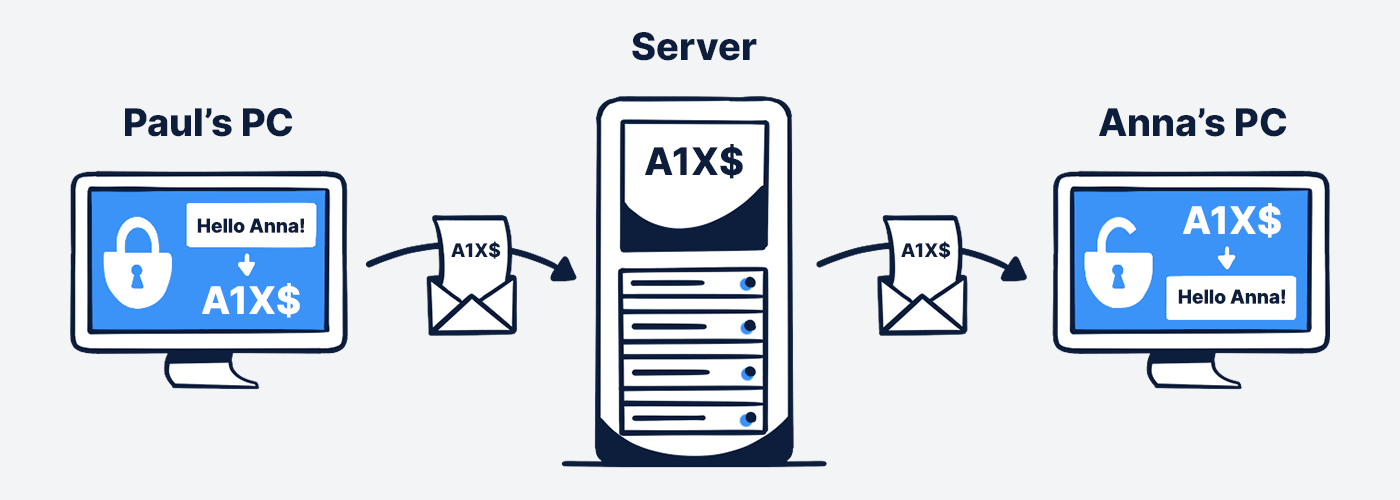
With a client-side end-to-end encryption, the data from user Paul is thus already encrypted in the browser during the upload, additionally transmitted encrypted with SSL certificate, stored encrypted on the server and retrieved by user Anna in the same way.
The data is therefore only decrypted again when downloaded in the user's browser. This also means that the key used to encrypt and decrypt the data never leaves the client server.
However, the situation is quite different when data is encrypted on the server side. The data is stored on the server together with the key, so the provider can theoretically also decrypt it. Platform operators that do not offer end-to-end encryption thus have access to their users' data at any time, since they either possess the key or the data is not encrypted in the cloud in the first place.
It is therefore worth double-checking with the provider when deciding on a software. Some providers like to advertise end-to-end encryption, even though the method used is pure SSL encryption.
Stackfield's end-to-end encryption
To ensure the best possible security, Stackfield offers true end-to-end encryption – a combination of AES and RSA encryption, ensuring that no one is able to view the contents of chat messages, documents or tasks without authorization.
Find out how our end-to-end encryption works and what content we securely encrypt in our daily collaboration in our whitepaper.
Almost finished...Please click the link in the email and confirm your email adress to complete the subscription process.
Never miss a post. Get awesome insights in your inbox.