The need for information security has never been greater than in today’s digital age. Yet when it comes to how data can actually be kept safe, people are often left puzzled. This is no surprise. Terms like "keys" and "encryption" tend to sound like they’re part of a secret code.
That’s why we’re cutting through the confusion in this article. We’ll clearly explain what end-to-end encryption is, how it works, and – most importantly – why it plays such a critical role when it comes to protecting sensitive information.
What is end-to-end encryption?
End-to-end encryption (also known as E2EE) is a method of securing data so that only the sender and the intended recipient can read its contents. Before the data is even sent, it is encrypted on the sender’s device. It remains in this unreadable form throughout its journey and is only decrypted once it reaches the recipient.
In simple terms: no one except the sender and the recipient can access the message, not even the provider of the software or service being used. Even if someone were to gain access to the technical infrastructure involved in transmitting the message, all they’d see would be an incomprehensible mix of letters, numbers and symbols.
Think of it like sending a letter written in a secret language that only you and the recipient understand. Even if the letter were opened along the way, the content would be meaningless to anyone else. That’s exactly how end-to-end encryption works: only the sender and recipient can read the message – no one in between.
How does end-to-end encryption work?
At the core of end-to-end encryption lies a special method for making messages unreadable. Through specific rules and mathematical processes, information is transformed in such a way that only the intended recipient can understand it. There are two fundamental ways in which encryption can be implemented:
- Symmetric Encryption (e. g. AES encryption):
In symmetric encryption, the same key is used for both encrypting and decrypting the data. You can think of it like a safe that is locked and unlocked with a single key. The sender locks the safe containing sensitive information and delivers it to the recipient, who uses the exact same key to open it.
The drawback: The key itself needs to be transferred from sender to recipient – and that is where a major security risk comes in. If someone intercepts the key in transit, the data is no longer safe.
The same issue arises if both sender and recipient already have matching keys. If one party loses the key or it gets stolen, a third party could use it to unlock the safe.
- Asymmetric Encryption (e. g. RSA encryption):
Asymmetric encryption works differently. Instead of a single key, it uses a key pair: a public key and a private key. The public key is used to encrypt the data, while the private key is required to decrypt it. The two keys are mathematically linked but cannot be used interchangeably.
Because of this separation, the public key can be shared freely – anyone can use it to encrypt a message. However, only the recipient, who possesses the corresponding private key, can decrypt and read the message. This means that even if there are many senders with access to the public key, only the holder of the private key can access the actual content.
A helpful analogy is a locked mailbox: anyone can drop a letter in through the slot (using the public key), but only the mailbox owner can unlock it and retrieve the message (using the private key).
AES encryption
AES, or Advanced Encryption Standard, is the world’s most widely used method for symmetric encryption. Developed by the U.S. National Institute of Standards and Technology, AES is still considered highly secure, as long as it is implemented correctly.
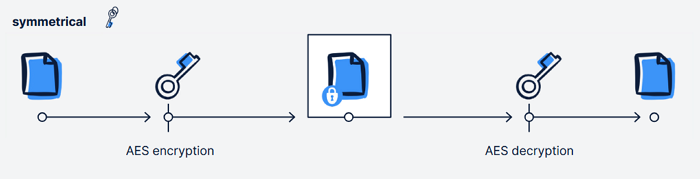
How AES Encryption Works
AES operates on a block basis. Data is broken into small chunks (called blocks) and transformed multiple times using complex mathematical steps. This process is so intricate that reversing it without the correct key is virtually impossible, even with immense computing power. The most common version uses a 256-bit key, offering more possible combinations than there are atoms in the universe.
What are the pros and cons of AES?
Pros:
- Very secure with proper key management
- Extremely fast and efficient
- Widely supported across platforms and systems
Cons:
- Key exchange must be secured
- Offers no protection if the key is stolen
- Not ideal for secure communication between strangers
RSA encryption
RSA (named after its inventors Ronald L. Rivest, Adi Shamir, and Leonard Adleman) is the most well-known and commonly used method of asymmetric encryption. It was developed in the 1970s and remains the foundation for many secure digital communications, like online banking or encrypted email.
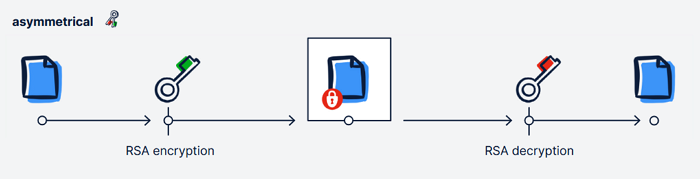
How RSA Encryption Works
RSA relies on a mathematical principle that is easy to compute in one direction but extremely difficult to reverse. In practice, that means it’s simple to create a secure, encrypted message but nearly impossible to decrypt it without the correct key. Without the private key, decrypting the message would require tremendous computing power and time.
Because RSA is relatively slow, it is not typically used to encrypt full messages. Instead, it is often used to securely transmit smaller pieces of information, such as a symmetric AES key – which can then be used to encrypt the actual message efficiently.
What are the pros and cons of RSA?
Pros:
- Secure key exchange between parties
- Enables communication without prior contact
- Can be combined with other methods like AES
Cons:
- Slower than symmetric encryption
- Computationally intensive, especially with long keys
- More complex to implement
How Stackfield combines both methods
To ensure the highest level of security during data transmission, Stackfield combines AES and RSA encryption into a fully-fledged end-to-end encryption system. The two methods are layered together in the following way:
- Initial Encryption with AES: All content is encrypted directly on the sender’s device using a randomly generated AES key. "Randomly generated" means that every new room created in Stackfield receives a unique, one-time AES key that is used to encrypt all messages within that room.
When it comes to files, Stackfield takes things a step further. For every individual file transfer, a completely new and unique AES key is generated—independent of the room key. This entire process happens automatically on the user’s device without any manual input.
- Additional Layer of Security with RSA: The AES key used to encrypt the content is itself encrypted with the recipient’s public RSA key. This means the data is effectively double-locked.
- Decryption by the Recipient: The recipient uses their private RSA key to decrypt the AES key, which then gives them access to the actual content. This ensures that only the intended recipient can read the data.
Even Stackfield, as the platform operator, never has access to the user’s private RSA keys or unencrypted content. All keys remain strictly on the users’ devices – making third-party access technically impossible.
Why is a genuine end-to-end encryption especially secure?
Many services claim to offer encryption, but in reality, the message is only encrypted during transmission. Once the message arrives at the provider’s server, it is decrypted – meaning the content becomes readable again. This opens the door to potential access by the provider itself, its employees or attackers who manage to breach the system.
True end-to-end encryption works differently:
- The content is encrypted before it leaves the sender’s device and remains protected during transmission.
- Decryption happens only on the recipient’s device.
- No one in between has access, not even the service provider.
This level of protection is absolutely essential in sensitive environments such as business communication, project management, or when handling legal or medical data. After all, what is the point of encryption if the provider can still read your messages?
The combination of AES (for strong and fast encryption) with RSA (for secure key exchange) creates a robust shield that reflects the state of the art in modern cryptography.
Conclusion: The key to real information security
"Two are better than one" – a phrase that holds true for encryption, too. By using multiple layers of protection, Stackfield ensures that your data is accessible only to those who are meant to see it and no one else.
Almost finished...Please click the link in the email and confirm your email adress to complete the subscription process.
Never miss a post. Get awesome insights in your inbox.